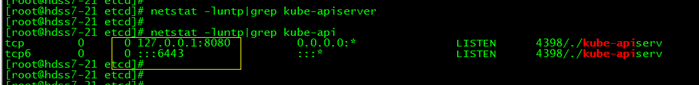
根据前面的规划,hdss7-21(10.4.7.21) hdss7-22(10.4.7.22) 这两台上面都要部署apiserver kubernetes 的 github地址:https://github.com/kubernetes/kubernetes https://github.com/kubernetes/kubernetes/tags 我们用的kubernets版本是 1.5.2 下载地址:https://github.com/kubernetes/kubernetes/releases/tag/v1.15.2 由于某些原因,有可能下载不了。 其他下载地址:http://106.12.88.74/softdown/k8s1.5/kubernetes-server-linux-amd64-v1.15.2.tar.gz +++++++++++++++++++ 10.4.7.21 上面部署apiserver 上传文件到10.4.7.21并解压 tar xf kubernetes-server-linux-amd64-v1.15.2.tar.gz -C /opt cd /opt mv kubernetes kubernetes-v1.15.2 ln -s /opt/kubernetes-v1.15.2 /opt/kubernetes cd /opt/kubernetesrm -rf kubernetes-src.tar.gz
在这个目录下面 /opt/kubernetes/server/bin cd /opt/kubernetes/server/bin rm -rf *.tar && rm -rf *_tag
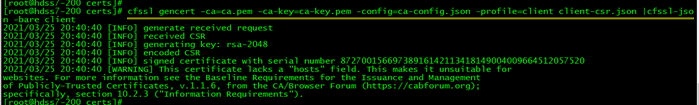
一、在部署之前,还是需要在 hdss7-200(10.4.7.200)上面签发证书: +++++++++ 在 10.4.7.200 上面操作 签发client 证书, apiserver 和 etcd 集群通信时会用到这个证书。 创建生成证书签名请求(csr)的 JSON 配置文件 vim /opt/certs/client-csr.json { "CN": "k8s-node", "hosts": [ ], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "beijing", "L": "beijing", "O": "od", "OU": "ops" } ] } 签发证书: cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=client client-csr.json |cfssl-json -bare client
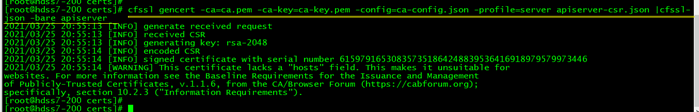
+++++++++++= 签发kube-apiserver证书(外部来访问apiserver 也需要证书验证) 创建生成证书签名请求(csr)的JSON配置文件 vim /opt/certs/apiserver-csr.json { "CN": "k8s-apiserver", "hosts": [ "127.0.0.1", "192.168.0.1", "kubernetes.default", "kubernetes.default.svc", "kubernetes.default.svc.cluster", "kubernetes.default.svc.cluster.local", "10.4.7.10", "10.4.7.21", "10.4.7.22", "10.4.7.23" ], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "beijing", "L": "beijing", "O": "od", "OU": "ops" } ] } ### apiserver可能存在的地址都要写上,上面10.4.7.10是vip,因为我们的环境是部署了两台apiserver cd /opt/certs 签发证书: cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=server apiserver-csr.json |cfssl-json -bare apiserver
++++++++++++ 二、开始正式部署apiserver ,在 10.4.7.21 上面操作: 把刚才签发的证书复制过来 cd /opt/kubernetes/server/bin mkdir cert && cd cert scp hdss7-200:/opt/certs/ca.pem . scp hdss7-200:/opt/certs/ca-key.pem . scp hdss7-200:/opt/certs/client.pem . scp hdss7-200:/opt/certs/client-key.pem . scp hdss7-200:/opt/certs/apiserver.pem . scp hdss7-200:/opt/certs/apiserver-key.pem .
cd /opt/kubernetes/server/bin mkdir conf && cd conf vi audit.yaml ##(apiserver 启动的时候会有一些日志审计,必须要有这个) apiVersion: audit.k8s.io/v1beta1 kind: Policy omitStages: - "RequestReceived" rules: - level: RequestResponse resources: - group: "" resources: ["pods"] - level: Metadata resources: - group: "" resources: ["pods/log", "pods/status"] - level: None resources: - group: "" resources: ["configmaps"] resourceNames: ["controller-leader"] - level: None users: ["system:kube-proxy"] verbs: ["watch"] resources: - group: "" resources: ["endpoints", "services"] - level: None userGroups: ["system:authenticated"] nonResourceURLs: - "/api*" - "/version" - level: Request resources: - group: "" resources: ["configmaps"] namespaces: ["kube-system"] - level: Metadata resources: - group: "" # core API group resources: ["secrets", "configmaps"] - level: Request resources: - group: "" - group: "extensions" - level: Metadata omitStages: - "RequestReceived" 创建apiserver 启动脚本: cd /opt/kubernetes/server/bin vim /opt/kubernetes/server/bin/kube-apiserver.sh #!/bin/bash ./kube-apiserver \ --apiserver-count 2 \ --audit-log-path /data/logs/kubernetes/kube-apiserver/audit-log \ --audit-policy-file ./conf/audit.yaml \ --authorization-mode RBAC \ --client-ca-file ./cert/ca.pem \ --requestheader-client-ca-file ./cert/ca.pem \ --enable-admission-plugins NamespaceLifecycle,LimitRanger,ServiceAccount,DefaultStorageClass,DefaultTolerationSeconds,MutatingAdmissionWebhook,ValidatingAdmissionWebhook,ResourceQuota \ --etcd-cafile ./cert/ca.pem \ --etcd-certfile ./cert/client.pem \ --etcd-keyfile ./cert/client-key.pem \ --etcd-servers https://10.4.7.12:2379,https://10.4.7.21:2379,https://10.4.7.22:2379 \ --service-account-key-file ./cert/ca-key.pem \ --service-cluster-ip-range 192.168.0.0/16 \ --service-node-port-range 3000-29999 \ --target-ram-mb=1024 \ --kubelet-client-certificate ./cert/client.pem \ --kubelet-client-key ./cert/client-key.pem \ --log-dir /data/logs/kubernetes/kube-apiserver \ --tls-cert-file ./cert/apiserver.pem \ --tls-private-key-file ./cert/apiserver-key.pem \ --v 2 调整权限,创建目录。 chmod +x /opt/kubernetes/server/bin/kube-apiserver.sh mkdir -p /data/logs/kubernetes/kube-apiserver/ 创建supervisor配置文件 vi /etc/supervisord.d/kube-apiserver.ini [program:kube-apiserver-7-21] command=/opt/kubernetes/server/bin/kube-apiserver.sh numprocs=1 directory=/opt/kubernetes/server/bin autostart=true autorestart=true startsecs=30 startretries=3 exitcodes=0,2 stopsignal=QUIT stopwaitsecs=10 user=root redirect_stderr=true stdout_logfile=/data/logs/kubernetes/kube-apiserver/apiserver.stdout.log stdout_logfile_maxbytes=64MB stdout_logfile_backups=4 stdout_capture_maxbytes=1MB stdout_events_enabled=false ####++++++++++ supervisorctl update
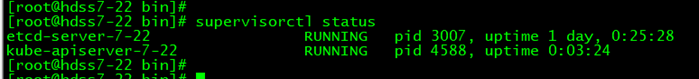
supervisorctl status
### hdss7-22(10.4.7.22)安装部署过程与10.4.7.21 一样。 不再要再在10.7.200 上面去签发证书了,前面已经做好了。 vim /etc/supervisord.d/kube-apiserver.ini
其他都一样。 supervisorctl status