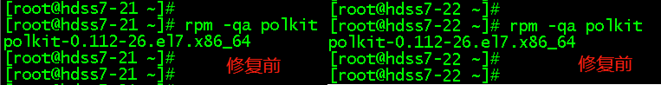
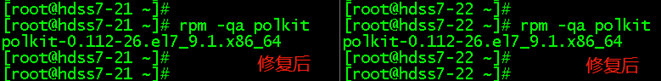
加密hosts文件 --vault-password-file参数使用 将服务器IP、用户名和密码写在/etc/ansible/hosts文件里面,如果是普通用户,服务器上必须要开启sudo权限,ansible_ssh_pass 和 ansible_become_pass 为同一个密码。用户密码尽量不要包含# " ' 一、加密host文件 加密前:ansible-vault /etc/ansible/hosts ##回车,输入密码 加密后:
ansible-vault edit /etc/ansible/hosts ##编辑hosts文件。 二、vault-password-file参数配置 vim /etc/ansible/ansible.cfg
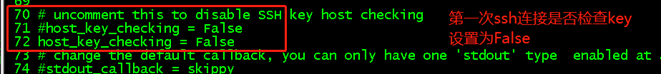
保存退出 创建这个密码文件,把密码写入进去 cd /etc/ansible echo "Dddskki@1554">.vault_file chmod a-w .vault_file chattr +i .vault_file vim /etc/profile ## 设置一个变量,值为.vault_file的绝对路径 ##文件的最后添加: export vault_file=/etc/ansible/.vault_file ##保存退出 source /etc/profile 三、调用测试 命令行测试: ansible-playbook /etc/ansible/var-polkit6-test.yaml --extra-vars 'polhosts=s8' --vault-password-file=$vault_file cat /etc/ansible/var-polkit6-test.yaml - hosts: '{{ polhosts }}' become: yes become_user: root become_method: sudo tasks: - name: test connection ping:
shell脚本调用测试:/root/pol_jm.sh #!/bin/bash #提示信息 print_help(){ echo "------------------------------------" echo " Usage: $0 xxx " echo "------------------------------------" exit 1 } if [ $# -ne 1 ];then clear echo "输入的参数不对,参数有且只有一个。" print_help fi OSVER7=`ansible $1 -m shell -a "cat /etc/redhat-release"|grep "release 7"` OSVER6=`ansible $1 -m shell -a "cat /etc/redhat-release"|grep "release 6"` if [[ ! -z $OSVER7 ]];then ansible-playbook /etc/ansible/var-polkit7.yaml --extra-vars "polhosts=$1" --vault-password-file=$vault_file fi if [[ ! -z $OSVER6 ]];then ansible-playbook /etc/ansible/var-polkit6.yaml --extra-vars "polhosts=$1" --vault-password-file=$vault_file fi #######+++######### /etc/ansible/var-polkit6.yaml - hosts: '{{ polhosts }}' become: yes become_user: root become_method: sudo tasks: - name: Copy polkit package and script file copy: src=/opt/polkit-0.96-11.el6_10.2.x86_64.rpm dest=/tmp/ - name: Run (local)script script: /root/polkit_xf.sh
/etc/ansible/var-polkit7.yaml - hosts: '{{ polhosts }}' become: yes become_user: root become_method: sudo tasks: - name: Copy polkit package and script file copy: src=/opt/polkit-0.112-26.el7_9.1.x86_64.rpm dest=/tmp/ - name: Run (local)script script: /root/polkit_xf.sh
/root/polkit_xf.sh ##polkit修复脚本 #!/bin/bash ##polkit 漏洞修复 #2022-02-18 POL=`rpm -qa polkit` C7POLKIT="/tmp/polkit-0.112-26.el7_9.1.x86_64.rpm" C6POLKIT="/tmp/polkit-0.96-11.el6_10.2.x86_64.rpm" OSVER7=`cat /etc/redhat-release |awk '{print $4}'| awk -F [.] '{print $1}'` OSVER6=`cat /etc/redhat-release |awk '{print $3}'| awk -F [.] '{print $1}'` function polkit_check(){ clear date if [[ $POL == "polkit-0.112-26.el7_9.1.x86_64" ]]; then echo "此系统的polkit漏洞已修复好,不用重复执行脚本。" exit fi if [[ $POL == "polkit-0.96-11.el6_10.2.x86_64" ]]; then echo "此系统的polkit漏洞已修复好,不用重复执行脚本。" exit fi } function polkit_xf(){ polkit_check if [[ ! -z $POL ]]; then if [ $OSVER7 -eq 7 ];then rpm -Uvh $C7POLKIT --nodeps --force >/tmp/polkitxf.txt 2>&1 if [ $? -eq 0 ]; then echo "polkit 漏洞修复完成。" rm -f $C7POLKIT exit else echo -e "\033[31m polkit 漏洞修复失败,日志件/tmp/polkitxf.txt 。\033[0m" exit fi fi else echo "此系统未安装polkit,不用修复。" exit fi ####CentOS6 if [[ ! -z $POL ]]; then if [ $OSVER6 -eq 6 ];then rpm -Uvh $C6POLKIT --nodeps --force >/tmp/polkitxf.txt 2>&1 if [ $? -eq 0 ]; then echo "polkit 漏洞修复完成。" rm -f $C6POLKIT exit else echo -e "\033[31m polkit 漏洞修复失败,日志件/tmp/polkitxf.txt 。\033[0m" exit fi fi else echo "此系统未安装polkit,不用修复。" exit fi } polkit_xf ########### 单个主机测试: /root/pol_jm.sh s8
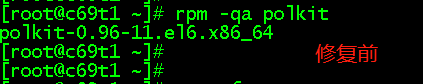
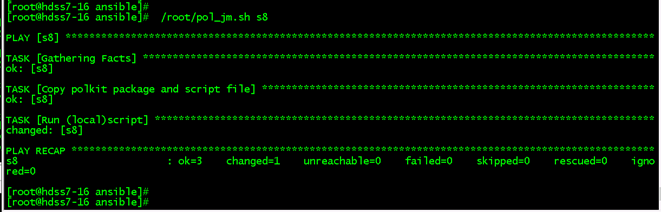
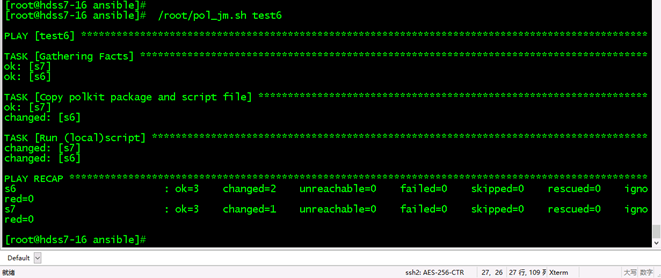
对一主机组测试:/root/pol_jm.sh test6